Stored XSS into HTML context with nothing encoded
Stored XSS into HTML context with nothing encoded
Web Security Academy #2
Lab: Stored XSS into HTML context with nothing encoded
Lab Description
Lab Level - APPRENTICE
This lab contains a stored cross-site scripting vulnerability in the comment functionality.
To solve this lab, submit a comment that calls the alert function when the blog post is viewed.
Step to Solve the Lab
- Access the lab by click on
ACCESS THE LAB. - After access the lab I saw a simple blog web page with some posts.
- As a normal user I visit one of the blog post and see there is a comment box.
- I post one comment and see how it take my input.
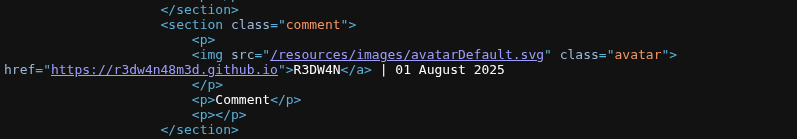
- After that I saw the source code. I found there are two place where my injected text is reflected.
- After conforming two place I inject a simple
htmltag in the comment box. Here is the payload :
1
<i>R3DW4N</i>
- I confirm
HTMLInjection
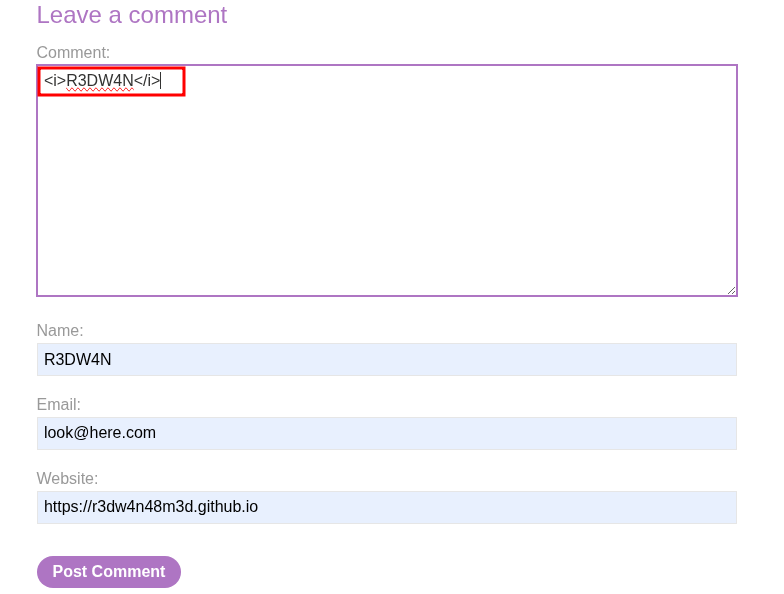
- After confirming HTML Injection, I inject a simple
xsspayload in the comment box with analertfunction.
1
<script>alert("R3DW4N")</script>
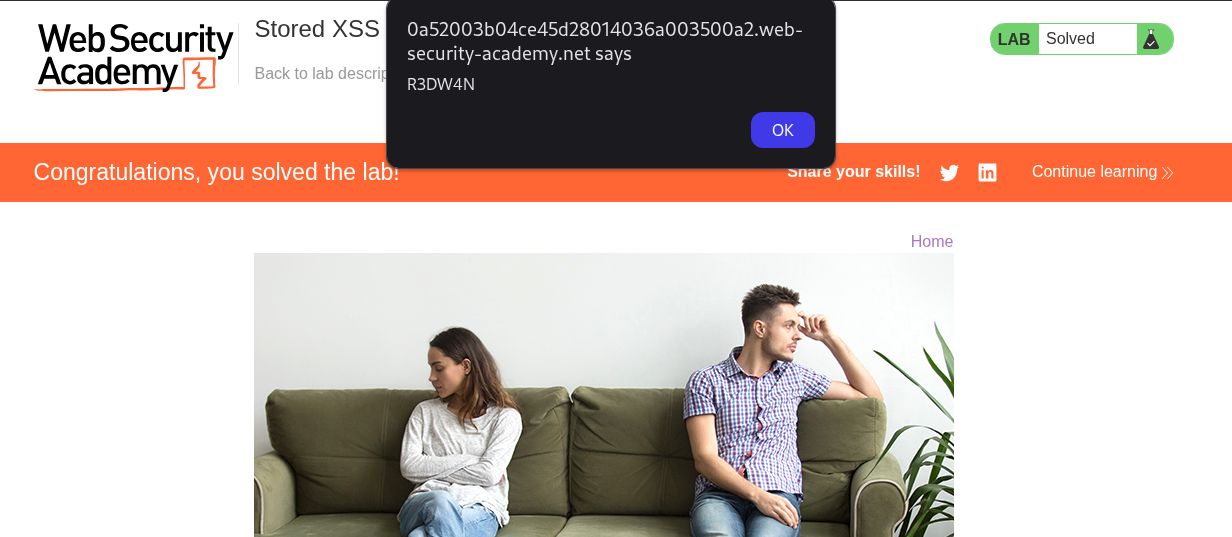
Congratulations, you solved the lab!
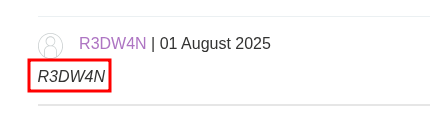
- Now every time a user visit the blog post that have the xss payload injected they will saw an
alertpopup. To confirm this I visit the same page that I inject xss payload and saw an alert withR3DW4Ntext.
And that’s it for this write-ups. If you want to connect with me, here are my social media links
I create a website where you can find more Bug Bounty Related Write-Ups. Here is the website link : Hacker-Write-Ups
Also I want to create a community where you can communicate with other hackers and much more fun stuff : We-Are-Anonymous
Assalamu alaikum wa rahmatullah.
This post is licensed under CC BY 4.0 by the author.